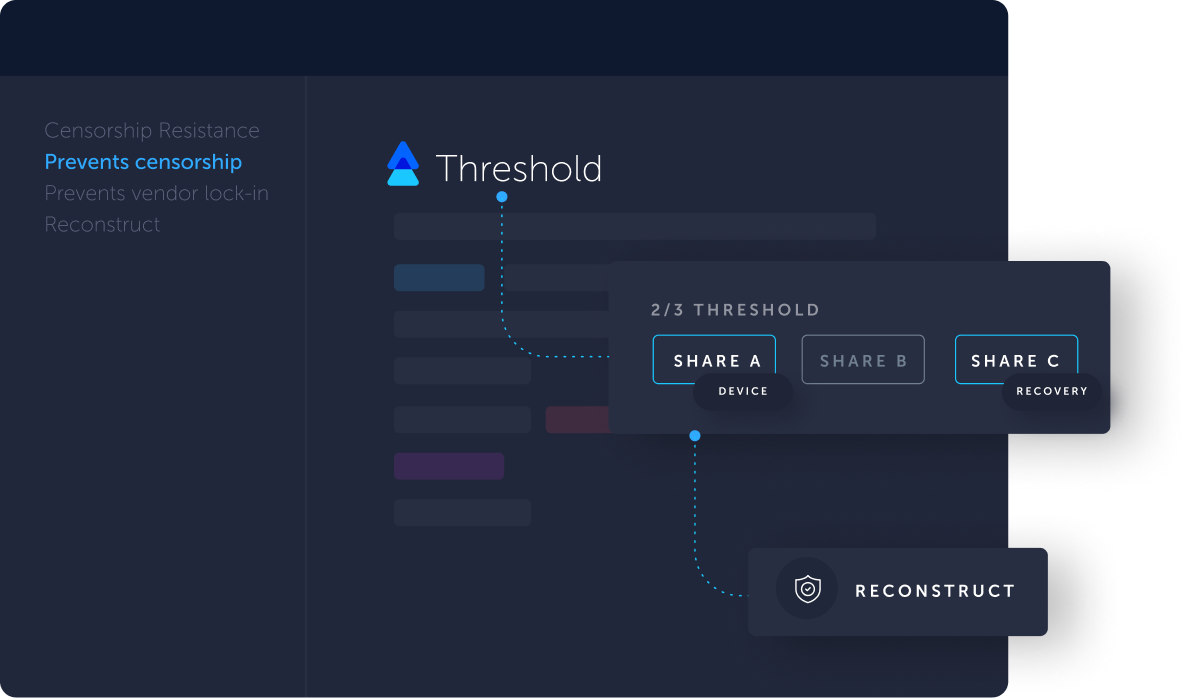
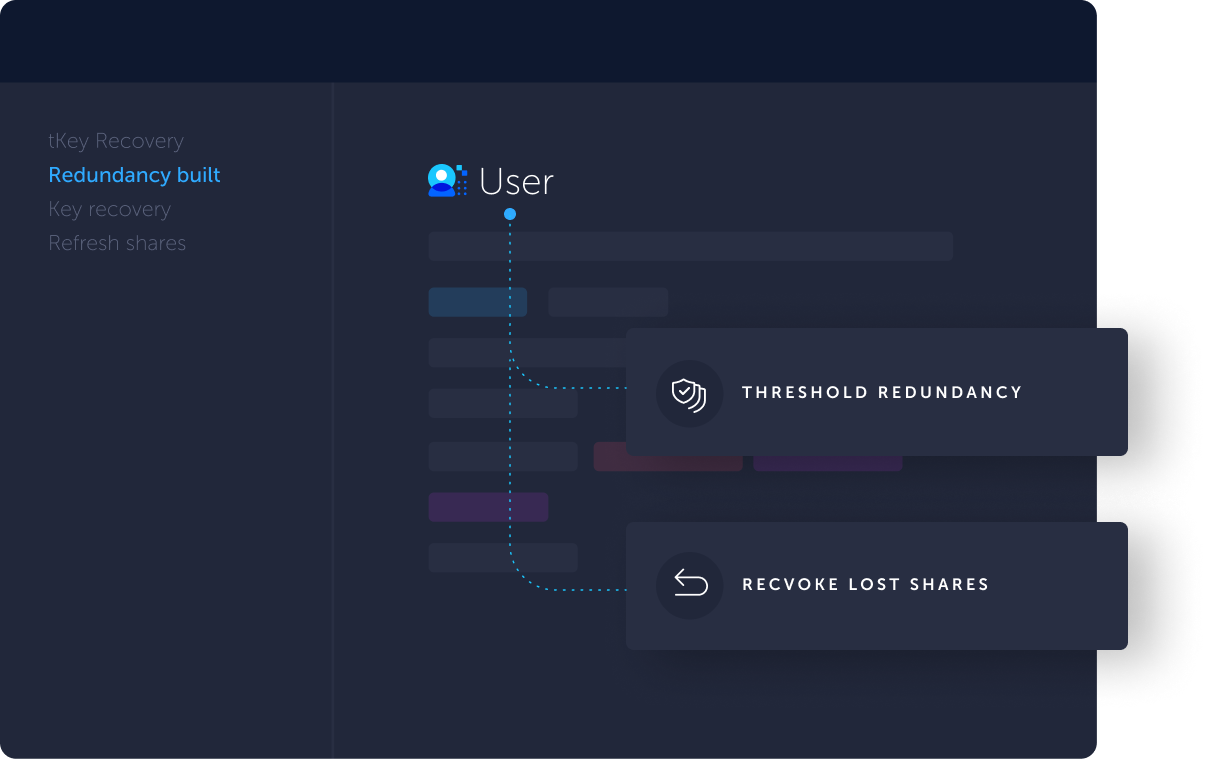
Error Message
Authentication via browser is limited to the cookies stored. Click to allow device storage backup.
Close
Warning Message
Authentication via browser is limited to the cookies stored. Click to allow device storage backup.
Close
Success Message
Authentication via browser is limited to the cookies stored. Click to allow device storage backup.
Close